
10 Privacy-Preserving AI Techniques for Cloud Security
Build compliant AI systems that protect sensitive data without sacrificing performance in cloud environments.

Written by
Adam Stewart
Key Points
- Combine federated learning with encryption for secure multi-organization collaboration
- Use homomorphic encryption to run computations on encrypted cloud data safely
- Apply differential privacy techniques to protect individual data points
- Balance strong privacy protection with maintaining optimal system performance
Protecting sensitive data in the cloud is crucial for organizations to maintain customer trust and comply with regulations. Privacy-preserving AI techniques enable secure data processing and analysis while safeguarding individual privacy.
Here are 10 key privacy-preserving AI techniques for cloud security:
- Differential Privacy: Adds controlled noise to datasets to protect individual privacy while enabling useful insights.
- Federated Learning: Enables collaborative model training without sharing raw data, keeping data private.
- Homomorphic Encryption: Allows computations on encrypted data without decrypting it first, ensuring data confidentiality.
- Secure Multi-Party Computation: Enables joint data analysis without revealing individual inputs, protecting privacy.
- Data Anonymization and Pseudonymization: Removes or replaces personal identifiers to protect user identities while allowing data sharing.
- Trusted Execution Environments: Secure, isolated environments for processing sensitive data.
- Confidential Cloud Computing: Keeps data encrypted while processed in the cloud.
- Privacy-Preserving Data Mining: Analyzes data while preserving confidentiality.
- Privacy-Preserving Machine Learning: Enables machine learning on private data.
- Blockchain for Privacy-Preserving AI: Decentralized, secure data sharing and auditing.
| Technique | Pros | Cons |
|---|---|---|
| Differential Privacy | Protects individual data points, enables accurate analysis | Adds random "noise" to data, may impact model accuracy |
| Federated Learning | Keeps user data private, enables collaborative learning | Requires significant computing resources, may have security vulnerabilities |
| Homomorphic Encryption | Allows computations on encrypted data, ensures data confidentiality | Computationally intensive, may be slow |
| Secure Multi-Party Computation | Enables joint computations on private data, ensures data confidentiality | Computationally intensive, may be slow |
| Data Anonymization and Pseudonymization | Protects user identities, allows data sharing | May not fully remove identifying info, risk of re-identification |
| Trusted Execution Environments | Provides a secure environment for data processing, ensures confidentiality | Limited availability, may require infrastructure changes |
| Confidential Cloud Computing | Enables secure data processing in the cloud, ensures confidentiality | May require infrastructure changes, limited availability |
| Privacy-Preserving Data Mining | Allows data analysis while preserving privacy, ensures confidentiality | May not suit all data types, limited availability |
| Privacy-Preserving Machine Learning (PPML) | Enables machine learning on private data, ensures confidentiality | May not suit all data types, limited availability |
| Blockchain for Privacy-Preserving AI | Enables decentralized, secure data sharing, ensures confidentiality | May have security vulnerabilities, limited scalability |
Choosing the right technique depends on your specific use case, data type, and infrastructure. Carefully evaluate each approach's strengths and weaknesses to determine the best fit for your cloud security needs.
Related video from YouTube
1. Differential Privacy
How It Works
Differential privacy protects individual privacy by adding a controlled amount of random "noise" to a dataset. This noise makes it difficult to identify specific individuals while still allowing useful insights from the overall data. The noise is carefully controlled to balance privacy and accuracy.
Advantages
- Strong Privacy Protection: Differential privacy mathematically guarantees that individual data points are kept private.
- Flexible: It can be used with various data types and analysis methods.
- Scalable: It works well with large datasets, making it suitable for cloud applications.
Limitations
- Privacy vs. Accuracy Trade-off: The added noise can reduce the accuracy of analysis results.
- Complex Implementation: Applying differential privacy requires significant expertise.
Cloud Security Use Cases
- Data Analysis: Analyze sensitive cloud data while protecting individual privacy.
- Machine Learning: Apply differential privacy to machine learning models to prevent privacy breaches.
- Secure Data Sharing: Enable organizations to share data securely while maintaining individual privacy.
2. Federated Learning
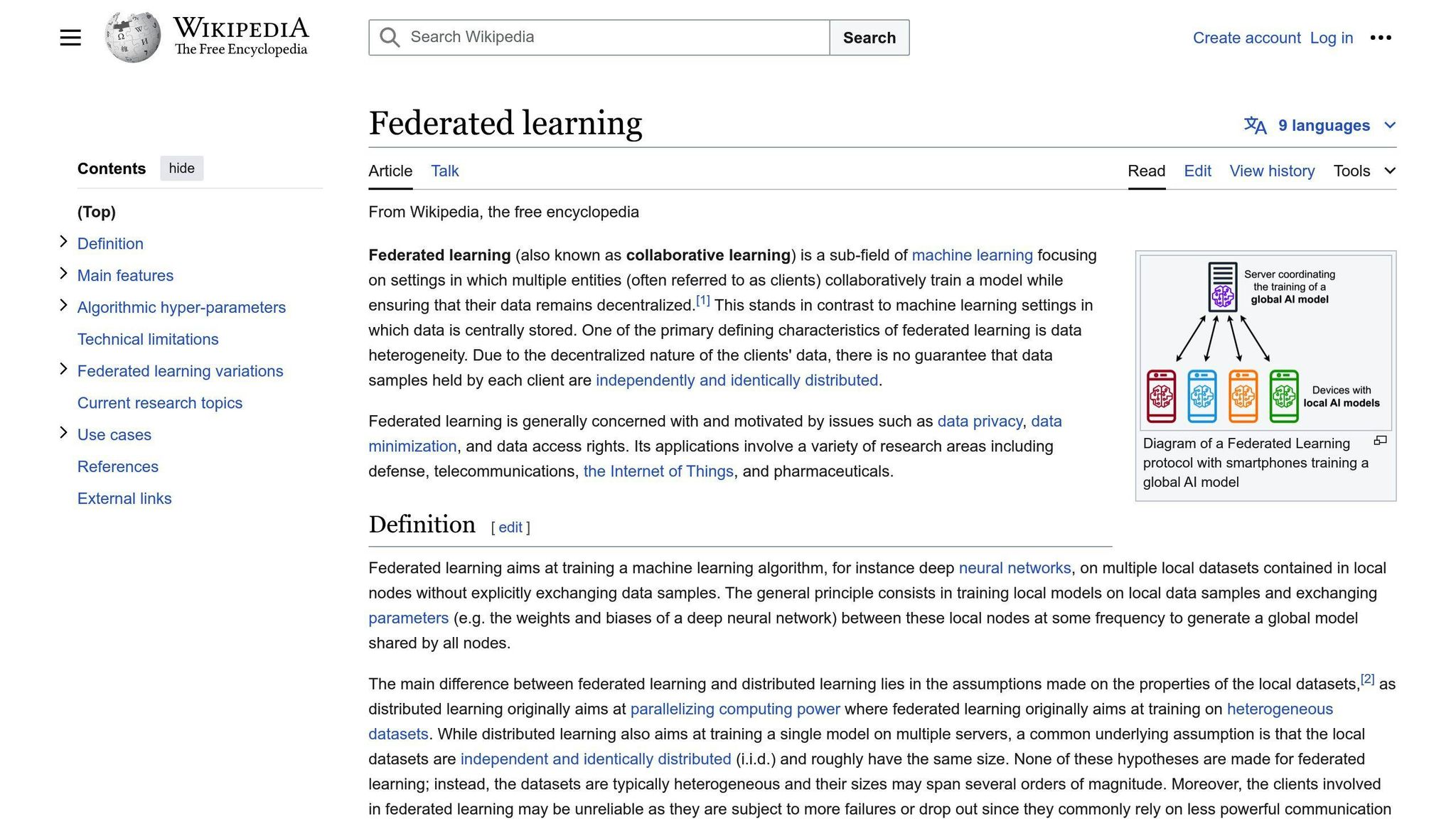
How It Works
Federated learning allows multiple organizations to jointly train a machine learning model without sharing their actual data. Each organization trains the model on their local data and only shares the model updates with a central server. The server combines these updates to create a new global model, which is sent back to each organization for further training. This process repeats until the desired model accuracy is achieved.
Benefits
- Preserves Data Privacy: Sensitive data remains private, as only model updates are shared, not the raw data itself.
- Improves Model Accuracy: By leveraging data from multiple sources, federated learning can produce more accurate models.
- Reduces Data Transfer: Only model updates are shared, resulting in increased bandwidth efficiency.
Challenges
- Complex Implementation: Federated learning requires expertise and infrastructure, especially in decentralized environments.
- Communication Overhead: The iterative process of sharing model updates can increase communication overhead.
Use Cases in Cloud Security
- Secure Data Analysis: Enable multiple organizations to collaboratively analyze data without sharing sensitive information.
- Privacy-Preserving AI: Apply federated learning to AI applications like image recognition and natural language processing to ensure privacy and security.
- Decentralized Data Sharing: Allow organizations to securely share data while maintaining individual privacy and control over their data.
| Benefit | Description |
|---|---|
| Data Privacy | Sensitive data remains private, as only model updates are shared |
| Improved Accuracy | Leveraging data from multiple sources can produce more accurate models |
| Bandwidth Efficiency | Reduced data transfer, as only model updates are shared |
| Challenge | Description |
|---|---|
| Complex Implementation | Requires expertise and infrastructure, especially in decentralized environments |
| Communication Overhead | Iterative process of sharing model updates can increase communication overhead |
3. Homomorphic Encryption
How It Works
Homomorphic encryption allows you to perform calculations on encrypted data without decrypting it first. The raw data remains fully encrypted while it's being processed, analyzed, and run through various algorithms. This enables you to keep data private while sharing it with third parties for computation.
Benefits
- Secure Cloud Usage: You can use cloud services without worrying about the security of your private data.
- Enables Collaboration: Organizations can share data while maintaining individual privacy and control.
- Regulatory Compliance: It helps ensure compliance with regulations in industries with strict data privacy rules.
Drawbacks
- Slow Computations: Homomorphic encryption requires intensive algorithms, making computations approximately a million times slower than traditional encryption. An operation that takes seconds could take eleven days.
Cloud Security Use Cases
Homomorphic encryption can be used in various cloud security applications, such as:
| Use Case | Description |
|---|---|
| Secure Data Analysis | Multiple organizations can collaboratively analyze data without sharing sensitive information. |
| Privacy-Preserving AI | Apply homomorphic encryption to AI applications like image recognition and natural language processing to ensure privacy and security. |
| Decentralized Data Sharing | Organizations can securely share data while maintaining individual privacy and control over their data. |
4. Secure Multi-Party Computation
Secure multi-party computation (MPC) is a way for multiple parties to work together on computing a function using their private data, without revealing their individual inputs. This approach allows collaboration on data analysis while keeping everyone's data confidential.
How It Works
Each party encrypts their data using a secret sharing scheme, splitting it into multiple parts. These encrypted parts are then shared among the parties, ensuring no single party has access to the complete data. The parties can perform computations on their respective parts, and the results are combined to get the final output.
Advantages
| Advantage | Description |
|---|---|
| Privacy | MPC ensures individual data remains confidential, even when shared with others. |
| Collaborative Analysis | MPC enables parties to jointly analyze data without compromising privacy. |
| Improved Accuracy | By combining data from multiple sources, MPC can lead to more accurate results. |
Limitations
| Limitation | Description |
|---|---|
| Computational Complexity | MPC requires complex algorithms, which can slow down computation times. |
| Scalability | MPC can be challenging to scale, especially with large datasets. |
Cloud Security Use Cases
MPC has various applications in cloud security, including:
- Data Sharing: MPC allows organizations to share data while maintaining individual privacy and control.
- Collaborative Threat Detection: MPC can detect threats and anomalies in cloud data without compromising privacy.
- Privacy-Preserving Machine Learning: MPC can be applied to machine learning algorithms to ensure data remains private while enabling model training and inference.
5. Data Anonymization and Pseudonymization
How It Works
Data Anonymization removes or alters personal identifiers from data to prevent individuals from being identified. Common techniques include:
- Data Masking: Replacing sensitive data with fictitious but realistic values, like replacing names with random names.
- Data Scrambling: Rearranging characters or values in data fields to break the link between data and individuals.
- Data Generalization: Replacing specific values with broader categories, like replacing an exact age with an age range.
Pseudonymization replaces direct identifiers with pseudonyms or artificial IDs. This allows data processing without revealing original identities, while maintaining a way to re-identify individuals if needed.
Benefits
| Benefit | Description |
|---|---|
| Data Utility | Anonymized and pseudonymized data can still be used for analysis, testing, etc., while protecting privacy. |
| Regulatory Compliance | Helps organizations comply with data privacy laws like GDPR and HIPAA by protecting personal data. |
| Reduced Risk | Minimizes the risk of data breaches exposing personal information. |
Limitations
| Limitation | Description |
|---|---|
| Re-identification Risk | Anonymized data could potentially be re-identified by combining it with other data sources or advanced techniques. |
| Data Distortion | Anonymization and pseudonymization can alter or distort the original data, potentially affecting analysis results. |
| Complexity | Implementing robust anonymization and pseudonymization techniques can be complex and resource-intensive. |
Cloud Security Use Cases
- Cloud Data Storage: Anonymize or pseudonymize sensitive data before storing it in the cloud to protect individual privacy.
- Cloud-Based Analytics: Use anonymized or pseudonymized data for analytics and machine learning in the cloud without exposing personal information.
- Secure Data Sharing: Share anonymized or pseudonymized data with third parties for collaboration or outsourcing while maintaining privacy.
6. Trusted Execution Environments
Trusted Execution Environments (TEEs) are secure areas within a computer's processor that run code and processes in an isolated, protected environment. This ensures sensitive data remains secure and separate from other software on the system.
How TEEs Work
TEEs use specialized hardware to encrypt data leaving the main memory and decrypt data returning before processing. This allows code and analytics to operate on unencrypted data within the secure environment. TEEs can scale well compared to other secure computation approaches. They also offer remote attestation, allowing remote clients to verify the integrity of code and data loaded in the TEE and establish a secure connection.
Benefits of TEEs
| Benefit | Description |
|---|---|
| End-to-End Security | TEEs provide end-to-end protection for data and applications, keeping sensitive data secure throughout its lifecycle. |
| Robust Security | TEEs offer strong security guarantees, including data integrity, code integrity, and data confidentiality. |
| Scalability | TEEs can scale well compared to other secure computation methods. |
Potential Drawbacks
| Drawback | Description |
|---|---|
| Implementation Complexity | Setting up robust TEEs can be complex and resource-intensive. |
| Vendor Dependence | TEEs are often vendor-specific, leading to dependence on a particular vendor. |
Cloud Security Use Cases
- Secure Cloud Computing: TEEs can provide end-to-end protection for data and applications in cloud computing environments.
- Data Analytics: TEEs can analyze sensitive data in a secure environment, ensuring data confidentiality.
- Secure Data Sharing: TEEs can enable sharing sensitive data with third parties while keeping data secure and confidential.
sbb-itb-93482ea
7. Confidential Cloud Computing
Confidential cloud computing is a technology that keeps an organization's sensitive data secure while it's processed and used in the cloud. It encrypts and stores the data in a secure area of a computer's processor called the Trusted Execution Environment (TEE).
How It Works
The TEE is an isolated, protected environment that runs code and processes separately from other software on the system. It uses specialized hardware to:
- Encrypt data leaving the main memory
- Decrypt data returning before processing
This allows code and analytics to operate on unencrypted data within the secure TEE environment, ensuring data confidentiality.
Benefits
| Benefit | Description |
|---|---|
| Enhanced Security | Confidential cloud computing adds an extra layer of security, protecting sensitive data from unauthorized access. |
| Secure Data Processing | It enables secure processing of sensitive data in the cloud, even when the data is in use. |
| Regulatory Compliance | It helps organizations comply with data privacy and security regulations like GDPR and HIPAA. |
Potential Drawbacks
| Drawback | Description |
|---|---|
| Complex Setup | Implementing confidential cloud computing can be complex and resource-intensive. |
| Vendor Dependence | The technology is often vendor-specific, leading to dependence on a particular vendor. |
Cloud Security Use Cases
1. Secure Cloud Computing: Confidential cloud computing can provide end-to-end protection for data and applications in cloud computing environments.
2. Data Analytics: It can analyze sensitive data in a secure environment, ensuring data confidentiality.
3. Secure Data Sharing: It can enable sharing sensitive data with third parties while keeping the data secure and confidential.
8. Privacy-Preserving Data Mining
How It Works
Privacy-preserving data mining (PPDM) allows analyzing data without revealing sensitive information. It uses techniques like encryption, data modification, and anonymization to protect the data's confidentiality while still enabling meaningful insights.
Benefits
| Benefit | Description |
|---|---|
| Data Privacy | PPDM keeps sensitive data confidential, even when shared with others. |
| Regulatory Compliance | It helps organizations follow data privacy laws like GDPR and HIPAA. |
| Useful Analysis | PPDM techniques can maintain data utility for accurate analysis and insights. |
Limitations
| Limitation | Description |
|---|---|
| Implementation Complexity | Setting up PPDM can be complex and resource-intensive. |
| Data Quality Impact | Applying PPDM techniques may affect data quality, leading to inaccurate insights. |
Cloud Security Use Cases
1. Secure Data Analysis: PPDM enables secure analysis of sensitive data in cloud environments.
2. Regulatory Compliance: It helps organizations comply with data privacy laws when storing and processing sensitive data in the cloud.
3. Secure Data Sharing: PPDM facilitates sharing sensitive data with third parties while maintaining confidentiality.
9. Privacy-Preserving Machine Learning (PPML)
How It Works
Privacy-Preserving Machine Learning (PPML) is a technique that allows collecting sensitive data while following privacy laws. It prevents data leaks from machine learning algorithms through a step-by-step approach. PPML protects data privacy during four stages:
- Model training
- Feeding input data into the model
- Providing output data from the model to the client
- Model privacy
Benefits
| Benefit | Description |
|---|---|
| Data Security | PPML safeguards sensitive data during machine learning processes, ensuring confidentiality and integrity. |
| Legal Compliance | It helps organizations follow data privacy laws like GDPR and HIPAA. |
| Accurate Analysis | PPML techniques can maintain data utility for accurate insights. |
Potential Drawbacks
| Drawback | Description |
|---|---|
| Complex Setup | Implementing PPML can be complicated and resource-intensive. |
| Data Quality Impact | Applying PPML techniques may affect data quality, leading to inaccurate insights. |
Cloud Security Use Cases
- Secure Model Training: PPML enables secure training of models on sensitive data in cloud environments.
- Private Data Analysis: It facilitates private data analysis and insights while maintaining data confidentiality.
- Compliant Data Sharing: PPML allows for compliant sharing of data with third parties while preserving privacy.
10. Blockchain for Privacy-Preserving AI
How It Works
Blockchain technology can enhance privacy in cloud security when combined with AI. This approach creates a decentralized AI system that separates personal data from non-personal data, effectively anonymizing user information. The system uses two independent blockchain networks:
- One network stores user information and data access permissions.
- Another network records an audit trail of all requests or queries made by users.
Benefits
Integrating blockchain and AI offers several advantages:
| Advantage | Description |
|---|---|
| User Privacy | User data remains private and secure, even when shared across multiple entities. |
| User Control | Users have complete authority over their data, enabling secure data sharing. |
| Transparency | Blockchain networks provide an immutable record of all transactions and requests. |
Cloud Security Use Cases
This integration has potential use cases in cloud security, including:
| Use Case | Description |
|---|---|
| Healthcare Data Sharing | Securely share medical records and patient information. |
| Private Data Analysis | Analyze sensitive data in cloud environments while preserving privacy. |
| Compliant Data Sharing | Share data with third parties while maintaining user privacy and compliance. |
Comparing Privacy-Preserving AI Techniques
Choosing the right privacy-preserving AI technique for cloud security is crucial. Here's a simple comparison of the pros and cons of each approach:
| Technique | Pros | Cons |
|---|---|---|
| Differential Privacy | Protects individual data points, enables accurate analysis | Adds random "noise" to data, may impact model accuracy |
| Federated Learning | Keeps user data private, enables collaborative learning | Requires significant computing resources, may have security vulnerabilities |
| Homomorphic Encryption | Allows computations on encrypted data, ensures data confidentiality | Computationally intensive, may be slow |
| Secure Multi-Party Computation | Enables joint computations on private data, ensures data confidentiality | Computationally intensive, may be slow |
| Data Anonymization and Pseudonymization | Protects user identities, allows data sharing | May not fully remove identifying info, risk of re-identification |
| Trusted Execution Environments | Provides a secure environment for data processing, ensures confidentiality | Limited availability, may require infrastructure changes |
| Confidential Cloud Computing | Enables secure data processing in the cloud, ensures confidentiality | May require infrastructure changes, limited availability |
| Privacy-Preserving Data Mining | Allows data analysis while preserving privacy, ensures confidentiality | May not suit all data types, limited availability |
| Privacy-Preserving Machine Learning (PPML) | Enables machine learning on private data, ensures confidentiality | May not suit all data types, limited availability |
| Blockchain for Privacy-Preserving AI | Enables decentralized, secure data sharing, ensures confidentiality | May have security vulnerabilities, limited scalability |
When choosing a technique, consider your specific use case, data type, and infrastructure. Each approach has its strengths and weaknesses, so carefully evaluate which one best meets your cloud security needs.
Keeping Cloud Data Safe with Privacy-Preserving AI
As we've explored various privacy-preserving AI techniques for cloud security, it's crucial to highlight the importance of implementing these methods to protect cloud-based systems and data. With the growing reliance on cloud computing, robust security measures are more essential than ever.
Privacy-preserving AI techniques offer a powerful solution to address data privacy and security concerns in the cloud. By adopting these techniques, organizations can ensure the confidentiality, integrity, and availability of their sensitive data while complying with regulatory requirements.
In today's digital world, data is a valuable asset, and its protection is paramount. By leveraging privacy-preserving AI techniques, businesses can build trust with customers, protect their reputation, and avoid the financial and legal consequences of data breaches.
When embarking on your cloud security journey, remember that privacy-preserving AI techniques are not a one-size-fits-all solution. It's crucial to evaluate your specific use case, data type, and infrastructure to determine the most suitable technique for your organization.
By exploring and adopting these innovative solutions, you can stay ahead in cloud security and ensure the integrity of your data in an increasingly complex digital landscape.
Comparing Privacy-Preserving AI Techniques
Choosing the right privacy-preserving AI technique for cloud security is crucial. Here's a simple comparison of the pros and cons of each approach:
| Technique | Pros | Cons |
|---|---|---|
| Differential Privacy | Protects individual data points, enables accurate analysis | Adds random "noise" to data, may impact model accuracy |
| Federated Learning | Keeps user data private, enables collaborative learning | Requires significant computing resources, may have security vulnerabilities |
| Homomorphic Encryption | Allows computations on encrypted data, ensures data confidentiality | Computationally intensive, may be slow |
| Secure Multi-Party Computation | Enables joint computations on private data, ensures data confidentiality | Computationally intensive, may be slow |
| Data Anonymization and Pseudonymization | Protects user identities, allows data sharing | May not fully remove identifying info, risk of re-identification |
| Trusted Execution Environments | Provides a secure environment for data processing, ensures confidentiality | Limited availability, may require infrastructure changes |
| Confidential Cloud Computing | Enables secure data processing in the cloud, ensures confidentiality | May require infrastructure changes, limited availability |
| Privacy-Preserving Data Mining | Allows data analysis while preserving privacy, ensures confidentiality | May not suit all data types, limited availability |
| Privacy-Preserving Machine Learning (PPML) | Enables machine learning on private data, ensures confidentiality | May not suit all data types, limited availability |
| Blockchain for Privacy-Preserving AI | Enables decentralized, secure data sharing, ensures confidentiality | May have security vulnerabilities, limited scalability |
When choosing a technique, consider your specific use case, data type, and infrastructure. Each approach has strengths and weaknesses, so carefully evaluate which one best meets your cloud security needs.
FAQs
What are the privacy-preserving techniques for AI?
Privacy-preserving AI techniques allow organizations to leverage the power of artificial intelligence and machine learning while safeguarding sensitive data. These methods ensure data confidentiality, integrity, and compliance with privacy regulations. Some key techniques include:
| Technique | Description |
|---|---|
| Differential Privacy | Adds controlled "noise" to datasets to protect individual privacy while enabling useful insights. |
| Federated Learning | Enables collaborative model training without sharing raw data, keeping data private. |
| Homomorphic Encryption | Allows computations on encrypted data without decrypting it first, ensuring data confidentiality. |
| Secure Multi-Party Computation | Enables joint data analysis without revealing individual inputs, protecting privacy. |
| Data Anonymization and Pseudonymization | Removes or replaces personal identifiers to protect user identities while allowing data sharing. |
Other techniques include:
- Trusted Execution Environments: Secure, isolated environments for processing sensitive data.
- Confidential Cloud Computing: Keeps data encrypted while processed in the cloud.
- Privacy-Preserving Data Mining: Analyzes data while preserving confidentiality.
- Privacy-Preserving Machine Learning: Enables machine learning on private data.
- Blockchain for Privacy-Preserving AI: Decentralized, secure data sharing and auditing.
Summarize with AI
Related Posts
AI in Healthcare: Balancing Patient Data Privacy & Innovation
Explore the benefits and risks of using AI in healthcare, along with strategies to balance patient data privacy and innovation. Learn how emerging technologies could shape the future of healthcare AI.
Privacy-Preserving Data Sharing: Guide for Edge Networks
Explore privacy-preserving data sharing techniques for edge networks. Learn about homomorphic encryption, secure multi-party computation, differential privacy, and federated learning. Discover real-world examples and implementation steps.
Homomorphic Encryption Guide: Secure Edge AI
Learn how homomorphic encryption secures sensitive data in edge AI systems. Explore benefits, challenges, and future outlook. Discover the importance of privacy preservation in edge AI.
Privacy Preserving AI Techniques: Complete 2025 Guide
Explore privacy-preserving AI techniques, benefits, core methods, and popular frameworks. Learn how to safeguard sensitive data while utilizing AI's benefits.
